to verify if your OUs are protected from accidental deletion use:
Get-ADOrganizationalUnit -Filter * -Properties * |Select-Object DistinguishedName, ProtectedFromAccidentalDeletion
to protect all OUs in AD from accidental deletion use:
Get-ADOrganizationalUnit -Filter * | Set-ADObject -ProtectedFromAccidentalDeletion:$true
27 January 2018
Protect OU (Organizational Unit) in AD from accidental deletion
Find FSMO roles from powershell
Get-ADDomainController -Filter * | Select-Object Name, Site, OperatingSystem, OperationMasterRoles
21 January 2018
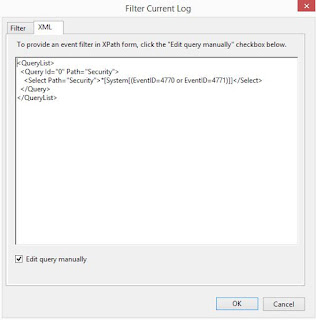
Search eventlogs with xml filter
# 4625 bad password in client log
# 4771 bad password in DC log
# 4740 lockout in DC log
# <Select Path="Security">*[System[(EventID=4740 or EventID=4771)]]</Select>
[xml]$XMLFilter = @"
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">*[System[(EventID=4740)]]</Select>
</Query>
</QueryList>
"@
$AllDomainControllers = Get-ADDomainController -Filter *
$AllEvents = @()
foreach($DC in $AllDomainControllers){
$Events = @()
$Events += Get-WinEvent -FilterXml $XMLFilter -ComputerName $DC.HostName -ErrorAction SilentlyContinue
$AllEvents += $Events
$DC.HostName + ' ' + $Events.Length
}
foreach($Event in $AllEvents){
$EventXMLData = [xml]$Event.ToXml()
for($i=0; $i -lt $EventXMLData.Event.EventData.Data.Count; $i++){
$Name = $EventXMLData.Event.EventData.Data[$i].Name
$Value = $EventXMLData.Event.EventData.Data[$i].'#text'
Add-Member -InputObject $Event -MemberType NoteProperty -Force -Name $Name -Value $Value
}
}
$AllEvents |
Select-Object TargetUsername, MachineName, TimeCreated,IpAddress, ID |
Format-Table
# 4771 bad password in DC log
# 4740 lockout in DC log
# <Select Path="Security">*[System[(EventID=4740 or EventID=4771)]]</Select>
[xml]$XMLFilter = @"
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">*[System[(EventID=4740)]]</Select>
</Query>
</QueryList>
"@
$AllDomainControllers = Get-ADDomainController -Filter *
$AllEvents = @()
foreach($DC in $AllDomainControllers){
$Events = @()
$Events += Get-WinEvent -FilterXml $XMLFilter -ComputerName $DC.HostName -ErrorAction SilentlyContinue
$AllEvents += $Events
$DC.HostName + ' ' + $Events.Length
}
foreach($Event in $AllEvents){
$EventXMLData = [xml]$Event.ToXml()
for($i=0; $i -lt $EventXMLData.Event.EventData.Data.Count; $i++){
$Name = $EventXMLData.Event.EventData.Data[$i].Name
$Value = $EventXMLData.Event.EventData.Data[$i].'#text'
Add-Member -InputObject $Event -MemberType NoteProperty -Force -Name $Name -Value $Value
}
}
$AllEvents |
Select-Object TargetUsername, MachineName, TimeCreated,IpAddress, ID |
Format-Table
Active directory domain user last logon date and time
"lastLogon" attribute is per domain controller - is not replicated to other domain controllers in the domain and each domain cotroller has his own information.
"lastLogonTimeStamp" is replicated in the domain (all domain controllers have the same updated information).
the date is stored in 100 miliseconds interval since 01.01.1601 (Juanuary 1, 1601)
to convert from System.Int64 we can use "FromFileTime" static method of DateTime class:
[System.DateTime]::FromFileTime($ADUser.lastlogon)
[System.DateTime]::FromFileTime($ADUser.lastlogontimestamp)
http://msdn.microsoft.com/en-us/library/ms676824(VS.85).aspx
http://msdn.microsoft.com/en-us/library/ms676823(VS.85).aspx
Active Directory Technical Specification
search the web for "MS-ADTS"
https://msdn.microsoft.com/en-us/library/cc223122.aspx
List active directory group membership changes
$ADGroup = Get-ADGroup -Identity 'Domain Admins'
Get-ADReplicationAttributeMetadata -Object $ADGroup.DistinguishedName -Server dc1 -ShowAllLinkedValues
in the output the "AttributeName" is the attribute that was changed - we should search for the "member" attribute.
"AttributeValue" is the value assigned to the attribute.
"FirstOriginatingCreateTime" is the time the value was added.
"LastOriginatingDeleteTime" is the time the value was deleted - but only if is different from "1/1/1601 2:00:00 AM"
Subscribe to:
Comments (Atom)